We are often asked whether an email about our services is real or fake.
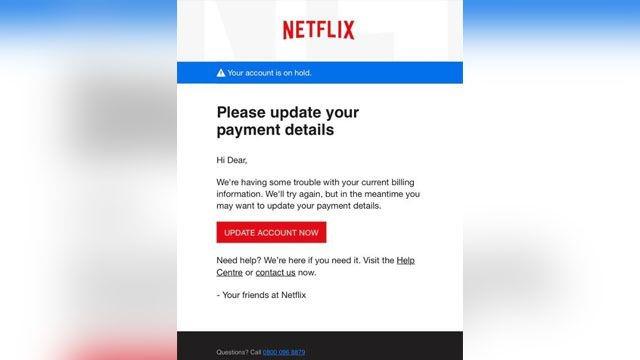
Deerfield Hosting will never send you a notice using any domain name other than deerfieldhosting.com or deerfieldhosting.net. That is a safe bet for any other company as well. Even beyond that common sense, any email which raises suspicions is probably from a criminal.
It’s a good idea to be cautious any time there is any suspicion at all. NEVER click on a link in any email or text unless you are expecting it, unless you know in advance what it is about. If you are uncertain and think it might be real, go to the company website directly – without clicking on the link.
This is called phishing. Most often the link will lead to a site set up to look like the company you are supposed to think it is. When you put in your login information, you have given them access to your account at that company.
I would take it a step further as well. Sometimes so called legitimate companies will send emails simply for the purpose of collecting information about you. The email or text will contain some sort of click bait. When you click on it you reveal personal information about yourself. This may then be used to sway a purchasing decision or perhaps worse, a political decision based on lies.
The US Federal Trade Commission explains this in more depth: https://consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams